Re: FBI Security Alerts
IKEA is battling an ongoing cyberattack where threat actors are targeting employees in internal phishing attacks using stolen reply-chain emails.
A reply-chain email attack is when threat actors steal legitimate corporate email and then reply to them with links to malicious documents that install malware on recipients' devices.
IKEA is warning employees of an ongoing reply-chain phishing cyber-attack targeting internal mailboxes. These emails are also being sent from other compromised IKEA organizations and business partners.
"There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organisations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA," explained an internal email sent to IKEA employees.
"This means that the attack can come via email from someone that you work with, from any external organisation, and as a reply to an already ongoing conversations. It is therefore difficult to detect, for which we ask you to be extra cautious."
IKEA IT teams warn employees that the reply-chain emails contain links with seven digits at the end and shared an example email
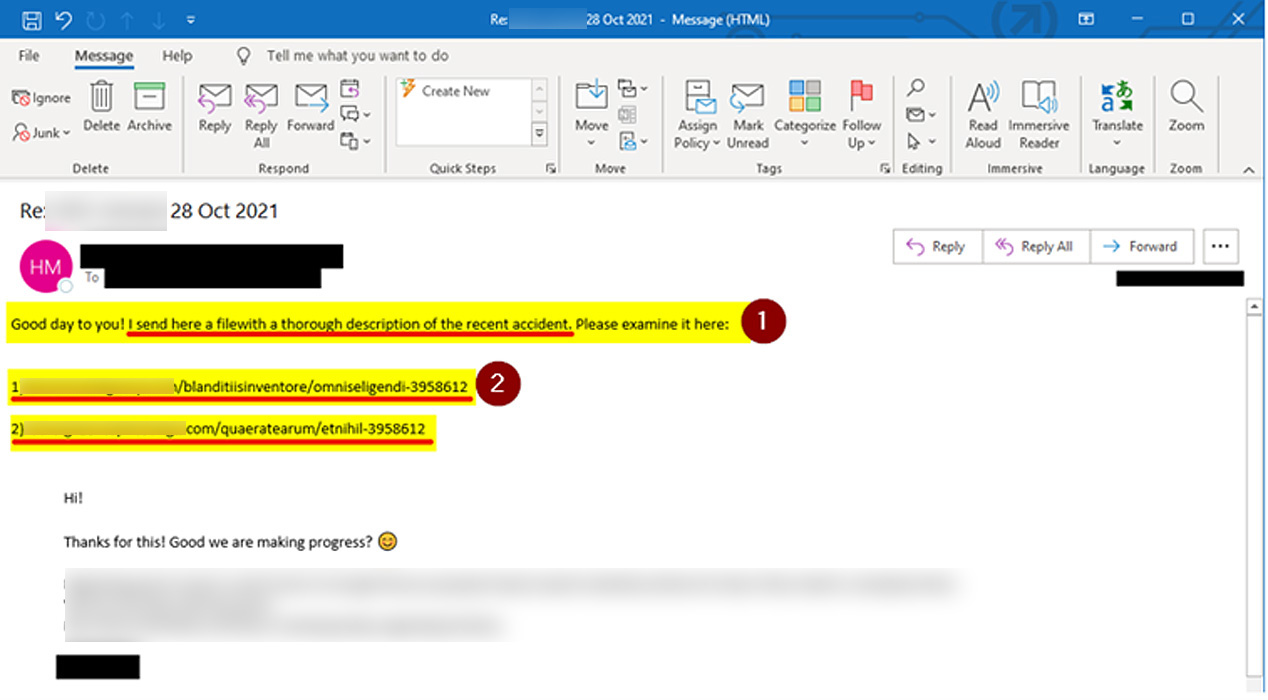
Threat actors have recently begun to compromise internal Microsoft Exchange servers using the ProxyShell and ProxyLogin vulnerabilities to perform phishing attacks.
Once they gain access to a server, they use the internal Microsoft Exchange servers to perform reply-chain attacks against employees using stolen corporate emails.
As the emails are being sent from internal compromised servers and existing email chains, there is a higher level of trust that the emails are not malicious.
Attack used to spread Emotet or Qbot trojan
The Qbot and Emotet trojans both lead to further network compromise and ultimately the deployment of ransomware on a breached network.
Due to the severity of these infections and the likely compromise of their Microsoft Exchange servers, IKEA is treating this security incident as a significant cyberattack that could potentially lead to a far more disruptive attack.
- November 26, 2021
IKEA is battling an ongoing cyberattack where threat actors are targeting employees in internal phishing attacks using stolen reply-chain emails.
A reply-chain email attack is when threat actors steal legitimate corporate email and then reply to them with links to malicious documents that install malware on recipients' devices.
IKEA is warning employees of an ongoing reply-chain phishing cyber-attack targeting internal mailboxes. These emails are also being sent from other compromised IKEA organizations and business partners.
"There is an ongoing cyber-attack that is targeting Inter IKEA mailboxes. Other IKEA organisations, suppliers, and business partners are compromised by the same attack and are further spreading malicious emails to persons in Inter IKEA," explained an internal email sent to IKEA employees.
"This means that the attack can come via email from someone that you work with, from any external organisation, and as a reply to an already ongoing conversations. It is therefore difficult to detect, for which we ask you to be extra cautious."
IKEA IT teams warn employees that the reply-chain emails contain links with seven digits at the end and shared an example email

Threat actors have recently begun to compromise internal Microsoft Exchange servers using the ProxyShell and ProxyLogin vulnerabilities to perform phishing attacks.
Once they gain access to a server, they use the internal Microsoft Exchange servers to perform reply-chain attacks against employees using stolen corporate emails.
As the emails are being sent from internal compromised servers and existing email chains, there is a higher level of trust that the emails are not malicious.
Attack used to spread Emotet or Qbot trojan
The Qbot and Emotet trojans both lead to further network compromise and ultimately the deployment of ransomware on a breached network.
Due to the severity of these infections and the likely compromise of their Microsoft Exchange servers, IKEA is treating this security incident as a significant cyberattack that could potentially lead to a far more disruptive attack.


Comment